Stay in complete control of who can view and modify your data
Security & control
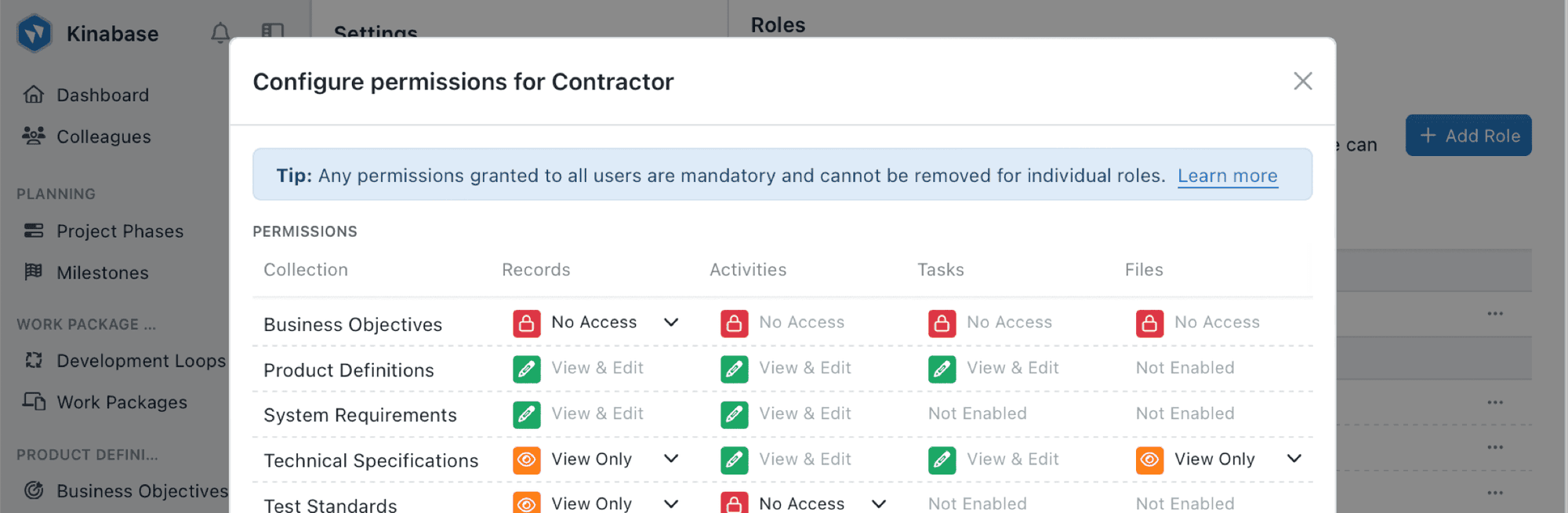
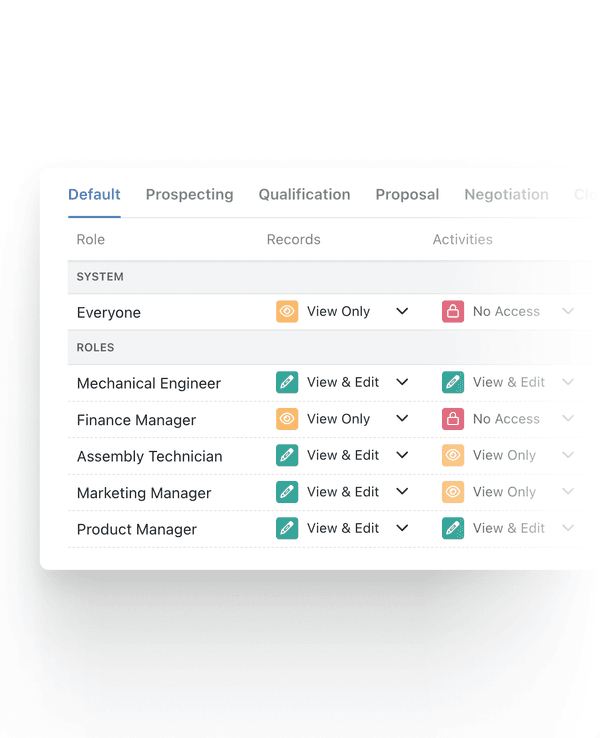
Role-based access control
Create roles that align with your business job titles, and assign permissions to suit your business needs.
Workflow integration
Use roles alongside workflows to ensure the right people play their part in your processes.
Granular permissions
Control who can view, edit, delete, and export records with precision and clarity.
Roles and permissions enable you to...
Control access and maintain security while keeping your team productive
Align with your business
Assign clear permissions
Control collection access
Protect sensitive data
Ensure productivity
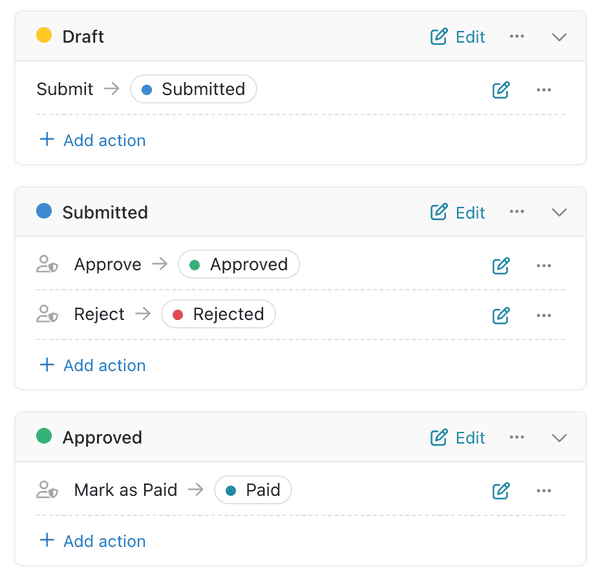
Workflow integration
Stage-based access
Control who can view and edit records at each stage of your workflow for better process management.
Rule enforcement
Set up rules, approvals, and signatures as part of your processes to maintain compliance.
Targeted visibility
Ensure team members only see records relevant to their role for increased focus and security.
Keep your information secure, and stay compliant
As an administrator, you can set up robust permissions, protecting access to sensitive information while maintaining operational flexibility.
Access control
Restrict who can import, export, or delete data, safeguarding your information from unauthorised access.
Full audit logging
Monitor your team's usage of Kinabase with comprehensive activity logs that track all changes.
Compliance ready
Remain compliant with industry regulations like GDPR, ISO 9001, and ISO 27001 with our secure framework.


